We might think that the 40 day and 40 night flood in the Book of Genesis was the only flood that could inflict unfathomable damage, but with the rapid evolution of massive DDoS attacks, we’re forced to see things in a new light. No, a DDoS attack isn’t capable of destroying the world as we know it, but for an online business without proper mitigation protection, it could certainly feel earth-shattering.
The entire year of 2014 has seen DDoS attacks get steadily bigger, stronger, faster and scarier for the owners of websites and businesses. The obvious and necessary solution is DDoS mitigation protection that’s bigger, stronger and faster than the attacks. And as a recent high-profile case demonstrated, that bigger, stronger, faster protection is working.
38 days later
It’s no coincidence that 38 days later sounds like the title of a horror movie. For one business, it very nearly was, as this is how long a gargantuan, non-stop multi-vector DDoS attack on their website lasted.
Though several targets were involved overall, the attack kept coming back to one specific video game site, believed to be the true target. This unnamed company was hit with massive network layer DDoS attacks, DNS floods, SYN floods, focused application layer (HTTP) floods, and dozens of SQLI and XSS attempts. Typically, attackers were using at least two attack vectors at once, escalating all the way up to five-vector attacks.
Even for internet security analysts and experts who are always prepared for the next frontier in DDoS attacks, this effort – which peaked at 110+ Gbps and 90+ million packets per second – was simply staggering. This wasn’t the work of malware or a bot or kid hackers with too much time on their hands. This was unimaginable time, money, resources and effort being put into the attempted destruction of a rival company.
But perhaps most staggering of all? For all 38 days, the attack was entirely mitigated. In the face of what would have been a crippling onslaught, the video game company’s web presence went unaffected for legitimate users.
Big problems require big solutions
Noah built the ark, and Incapsula built Behemoth.
Throughout 2013, Incapsula identified two major trends in DDoS attacks: the first was that these attacks were rapidly evolving, with multiple vectors routinely being used in a single attack, and the second was that DDoS attacks were ballooning in size, with several up over 100 Gbps.
With these trends in mind, Incapsula set out to offer an Infrastructure Protection service that could be activated on the fly and withstand even the highest-volume DDoS attacks.
This service is a variation on a tried-and-true method of a using BGP routing to provide DDoS protection. The advantage of this method is that the protection is completely versatile and can be applied to any type of device and communication protocol. This enables the company to protect not only websites but also other assets – from email services to gaming servers.
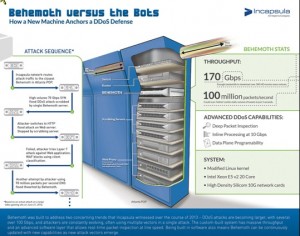
Incapsula’s twist is the Behemoth server, which boosts the old-school deployment option with latest deep traffic inspection capabilities and an ability to handle 170GBps worth of traffic an inline rate, which is a fancy-talk for “zero delays”.
As soon as the beginning of the 38-day attack was detected, the client made a border gateway patrol (BGP) announcement, which put Incapsula’s BGP-enabled DDoS protection services on the front lines of all incoming traffic.
Traffic-filtering duties went to the second major component of Incapsula’s infrastructure protection – the then newly-introduced Behemoth scrubbers. In the first 11 hours of the attack alone, the Behemoth scrubbers blocked a 70 Gbps SYN flood, an HTTP flood, a Layer 7 attack, and a 90-million packets per second DNS flood.
By the end of the 38-day attack, the Behemoth scrubbing servers had filtered 51,000+ terabits of malicious traffic. Meanwhile, legitimate traffic was passed through to the video gaming site using GRE tunneling, ensuring uninterrupted service for the company’s valued users.
Behemoth infrastructure for DDoS mitigation (source + Hi-Res image: Incapsula)
More to come
We can see the future of DDoS attacks, and the future is frankly hideous.
Bots are continuously becoming more sophisticated. They can now routinely bypass two of the most common bot filtering security challenges by accepting and storing cookies, and executing JavaScript. Additionally, massive SYN floods and DNS floods are already becoming the norm, and over 80% of DDoS attacks are now multi-vector.
Soon enough, mitigation will have to be a major focus of every online business’s security plan. With the way DDoS attacks are growing and evolving, mitigation is no longer optional, nor is it something that’s strictly for major corporations. Websites big and small require the right protection at the right time.